Ransom.Win32.MIMIC.D
Ransom:Win32/Mimic.MA!MTB (MICROSOFT)
Windows


恶意软件类型:
Ransomware
有破坏性?:
没有
加密?:
没有
In the Wild:
是的
概要
该勒索软件通过两种途径侵入系统:一是被其他恶意软件作为文件植入,二是用户访问恶意网站时在不知情的情况下下载的文件。
它不具备任何传播功能。
它不具备任何后门功能。
它会收集受感染计算机上的特定信息。
它会释放勒索说明文件作为赎金票据,并避免加密具有以下扩展名的文件:
技术详细信息
Arrival Details
该勒索软件通过两种途径侵入系统:一是被其他恶意软件作为文件植入,二是用户访问恶意网站时在不知情的情况下下载的文件。
Installation
该勒索软件会释放以下文件:
- %User Temp%\7ZipSfx.000\7za.exe → legitimate 7zip application, deleted afterwards
- %User Temp%\7ZipSfx.000\DC.exe → detected as HackTool.Win32.DEFENDERCONTROL.Z, deleted afterwards
- %User Temp%\7ZipSfx.000\ENC_default_default_2024-09-01_14-25-56=ELENOR-corp.exe → Mimic ransomware, deleted afterwards
- %User Temp%\7ZipSfx.000\Everything.exe → legitimate Everything application, deleted afterwards
- %User Temp%\7ZipSfx.000\Everything.ini → deleted afterwards
- %User Temp%\7ZipSfx.000\Everything2.ini → deleted afterwards
- %User Temp%\7ZipSfx.000\Everything32.dll → legitimate dll used by Everything.exe, deleted afterwards
- %User Temp%\7ZipSfx.000\Everything64.dll → password protected archive containing malicious payload, deleted afterwards
- %User Temp%\7ZipSfx.000\gui35.exe → deleted afterwards
- %User Temp%\7ZipSfx.000\gui40.exe → GUI used by Mimic ransomware, deleted afterwards
- %User Temp%\7ZipSfx.000\xdel.exe → legitimate sdelete application, deleted afterwards
- %User Temp%\7ZSfx000.cmd → used to delete the sample and itself
- Copy of files dropped in %User Temp%\7ZipSfx.000:
- %AppDataLocal%\{Generated GUID}\7za.exe
- %AppDataLocal%\{Generated GUID}\DC.exe
- %AppDataLocal%\{Generated GUID}\Everything.exe
- %AppDataLocal%\{Generated GUID}\Everything.ini
- %AppDataLocal%\{Generated GUID}\Everything2.ini
- %AppDataLocal%\{Generated GUID}\Everything32.dll
- %AppDataLocal%\{Generated GUID}\Everything64.dll
- %AppDataLocal%\{Generated GUID}\gui35.exe
- %AppDataLocal%\{Generated GUID}\gui40.exe
- %AppDataLocal%\{Generated GUID}\systemsg.exe → copy of ENC_default_default_2024-09-01_14-25-56=ELENOR-corp.exe
- %AppDataLocal%\{Generated GUID}\xdel.exe
- %AppDataLocal%\{Generated GUID}\session.tmp
- %AppDataLocal%\{Generated GUID}\global_options.ini
- %System%\GroupPolicy\Machine\Registry.pol
- %System%\GroupPolicy\gpt.ini
- %System Root%\temp\session.tmp
它会添加以下进程:
- %User Temp%\7ZipSfx.000\7za.exe i
- %User Temp%\7ZipSfx.000\7za.exe x -y -p{Archive File Password} Everything64.dll
- %User Temp%\7ZipSfx.000\ENC_default_default_2024-09-01_14-25-56=ELENOR-corp.exe
- cmd /c "%User Temp%\7ZSfx000.cmd"
- %AppDataLocal%\{Generated GUID}\systemsg.exe
- %AppDataLocal%\{Generated GUID}\gui40.exe
- %Program Files%\Everything\Everything.exe" -startup
- %AppDataLocal%\{Generated GUID}\DC.exe /D
- %AppDataLocal%\{Generated GUID}\systemsg.exe -e watch -pid {Current Process PID} -!
- %AppDataLocal%\{Generated GUID}\systemsg.exe" -e ul1;
- %AppDataLocal%\{Generated GUID}\systemsg.exe" -e ul2;
- powercfg.exe -H off
- powercfg.exe -SETACVALUEINDEX 8c5e7fda-e8bf-4a96-9a85-a6e23a8c635c 4f971e89-eebd-4455-a8de-9e59040e7347 7648efa3-dd9c-4e3e-b566-50f929386280 0
- powercfg.exe -SETACVALUEINDEX 8c5e7fda-e8bf-4a96-9a85-a6e23a8c635c 4f971e89-eebd-4455-a8de-9e59040e7347 96996bc0-ad50-47ec-923b-6f41874dd9eb 0
- powercfg.exe -SETACVALUEINDEX 8c5e7fda-e8bf-4a96-9a85-a6e23a8c635c 4f971e89-eebd-4455-a8de-9e59040e7347 5ca83367-6e45-459f-a27b-476b1d01c936 0
- powercfg.exe -SETDCVALUEINDEX 8c5e7fda-e8bf-4a96-9a85-a6e23a8c635c 4f971e89-eebd-4455-a8de-9e59040e7347 7648efa3-dd9c-4e3e-b566-50f929386280 0
- powercfg.exe -SETDCVALUEINDEX 8c5e7fda-e8bf-4a96-9a85-a6e23a8c635c 4f971e89-eebd-4455-a8de-9e59040e7347 96996bc0-ad50-47ec-923b-6f41874dd9eb 0
- powercfg.exe -SETDCVALUEINDEX 8c5e7fda-e8bf-4a96-9a85-a6e23a8c635c 4f971e89-eebd-4455-a8de-9e59040e7347 5ca83367-6e45-459f-a27b-476b1d01c936 0
- powercfg.exe -SETACVALUEINDEX e9a42b02-d5df-448d-aa00-03f14749eb61 4f971e89-eebd-4455-a8de-9e59040e7347 7648efa3-dd9c-4e3e-b566-50f929386280 0
- powercfg.exe -SETACVALUEINDEX e9a42b02-d5df-448d-aa00-03f14749eb61 4f971e89-eebd-4455-a8de-9e59040e7347 96996bc0-ad50-47ec-923b-6f41874dd9eb 0
- powercfg.exe -SETACVALUEINDEX e9a42b02-d5df-448d-aa00-03f14749eb61 4f971e89-eebd-4455-a8de-9e59040e7347 5ca83367-6e45-459f-a27b-476b1d01c936 0
- powercfg.exe -SETDCVALUEINDEX e9a42b02-d5df-448d-aa00-03f14749eb61 4f971e89-eebd-4455-a8de-9e59040e7347 7648efa3-dd9c-4e3e-b566-50f929386280 0
- powercfg.exe -SETDCVALUEINDEX e9a42b02-d5df-448d-aa00-03f14749eb61 4f971e89-eebd-4455-a8de-9e59040e7347 96996bc0-ad50-47ec-923b-6f41874dd9eb 0
- powercfg.exe -SETDCVALUEINDEX e9a42b02-d5df-448d-aa00-03f14749eb61 4f971e89-eebd-4455-a8de-9e59040e7347 5ca83367-6e45-459f-a27b-476b1d01c936 0
- powercfg.exe -S 8c5e7fda-e8bf-4a96-9a85-a6e23a8c635c
- powercfg.exe -S e9a42b02-d5df-448d-aa00-03f14749eb61
- ping 127.2 -n 5 & fsutil file setZeroData offset=0 length=20000000 \"%s\" & cd /d \"%s\" & Del /f /q /a *.exe *.bat
- ping 127.2 -n 5 & fsutil file setZeroData offset=0 length=20000000 \"%s\" & cd /d \"%s\" & Del /f /q /a *.exe *.ini *.dll *.bat *.db
- powershell.exe -ExecutionPolicy Bypass \"Get-VM | Stop-VM\"
- powershell.exe -ExecutionPolicy Bypass \"Get-VM | Select-Object vmid | Get-VHD | %{Get-DiskImage -ImagePath $_.Path; Get-DiskImage -ImagePath $_.ParentPath} | Dismount-DiskImage\"
- powershell.exe -ExecutionPolicy Bypass \"Get-Volume | Get-DiskImage | Dismount-DiskImage\"
- bcdedit.exe /set {default} bootstatuspolicy ignoreallfailures
- bcdedit.exe /set {default} recoveryenabled no
- wbadmin.exe DELETE SYSTEMSTATEBACKUP
- wbadmin.exe delete catalog -quiet
- reg add "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon" /v "AllowMultipleTSSessions" /t REG_DWORD /d 0x1 /f
- reg add "HKLM\system\CurrentControlSet\Control\Terminal Server" /v "fSingleSessionPerUser" /t REG_DWORD /d 0x0 /f
- reg add "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\sethc.exe" /v Debugger /t REG_SZ /d "c:\windows\system32\cmd.exe"
- notepad.exe %AppDataLocal%\Decrypt_ELENOR-corp_info.txt
- %AppDataLocal%\{Generated GUID}\xdel.exe -accepteula -p 1 -c {Encrypted Drive}
- wevtutil.exe cl security
- wevtutil.exe cl system
- wevtutil.exe cl application
- cmd.exe /d /c "ping 127.2 -n 5 & fsutil file setZeroData offset=0 length=20000000 "%AppDataLocal%\{Generated GUID}\systemsg.exe" & cd /d "%AppDataLocal%\{Generated GUID}" & Del /f /q /a *.exe *.ini *.dll *.bat *.db"
(Note: %User Temp% 是当前用户的临时文件夹,通常位于此路径 C:\Documents and Settings\{user name}\Local Settings\Temp 在Windows 2000(32位)、XP及Server 2003(32位)系统上,或 C:\Users\{user name}\AppData\Local\Temp on Windows Vista, 7, 8, 8.1, 2008(64-bit), 2012(64-bit) and 10(64-bit).. %AppDataLocal% 是本地应用程序数据文件夹, 通常位于此路径 C:\Documents and Settings\{user name}\Local Settings\Application Data 在Windows 2000(32位)、XP及Server 2003(32位)系统上,或 C:\Users\{user name}\AppData\Local on Windows Vista, 7, 8, 8.1, 2008(64-bit), 2012(64-bit) and 10(64-bit).. %Program Files% 是默认的程序安装文件夹, 通常位于此路径 C:\Program Files in Windows 2000(32-bit), Server 2003(32-bit), XP, Vista(64-bit), 7, 8, 8.1, 2008(64-bit), 2012(64-bit) and 10(64-bit) , or C:\Program Files (x86) in Windows XP(64-bit), Vista(64-bit), 7(64-bit), 8(64-bit), 8.1(64-bit), 2008(64-bit), 2012(64-bit) and 10(64-bit).)
它会创建以下文件夹:
- %User Temp%\7ZipSfx.000
- %AppDataLocal%\{Generated GUID} →File attribute set to HIDDEN and SYSTEM
- %System Root%\temp
(Note: %User Temp% 是当前用户的临时文件夹,通常位于此路径 C:\Documents and Settings\{user name}\Local Settings\Temp 在Windows 2000(32位)、XP及Server 2003(32位)系统上,或 C:\Users\{user name}\AppData\Local\Temp on Windows Vista, 7, 8, 8.1, 2008(64-bit), 2012(64-bit) and 10(64-bit).. %AppDataLocal% 是本地应用程序数据文件夹, 通常位于此路径 C:\Documents and Settings\{user name}\Local Settings\Application Data 在Windows 2000(32位)、XP及Server 2003(32位)系统上,或 C:\Users\{user name}\AppData\Local on Windows Vista, 7, 8, 8.1, 2008(64-bit), 2012(64-bit) and 10(64-bit).. %System Root% 此处指Windows系统根目录,其通常位于 C:\ 适用于所有Windows操作系统版本。)
它会添加以下互斥量,以确保在任何时候只有一个副本在运行:
- {Derived from the string "WhosYourBunny"}
Autostart Technique
该勒索软件会添加以下注册表项,以实现每次系统启动时自动执行:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Run
systemsg = %AppDataLocal%\{Generated GUID}\systemsg.exe
其他系统修改
该勒索软件会添加以下注册表项:
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\
exefile\shell\open\
command
(Default) = "%1" %*
HKEY_USER\S-1-5-21-2019512041-4230814187-3178073052-1000_CLASSES\exefile\
shell\open\command
(Default) = "%1" %*
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows Defender\Real-Time Protection
DisableRealtimeMonitoring = 1
HKEY_LOCAL_MACHINE\Software\Microsoft\
Windows\CurrentVersion\Policies\
Explorer
HidePowerOptions = 1
HKEY_CURRENT_USER\Software\Microsoft\
Windows\CurrentVersion\Policies\
Explorer
HidePowerOptions = 1
HKEY_CURRENT_USER\Software\Microsoft\
Windows\CurrentVersion\Policies\
Explorer
NoClose = 1
HKEY_CURRENT_USER\Software\Microsoft\
Windows\CurrentVersion\Policies\
Explorer
StartMenuLogOff = 1
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\
Control\FileSystem
LongPathsEnabled = 1
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Policies\
DataCollection
AllowTelemetry = 0
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows NT\CurrentVersion\Winlogon
AllowMultipleTSSessions = 1
HKEY_LOCAL_MACHINE\system\CurrentControlSet\
Control\Terminal Server
fSingleSessionPerUser = 0
HKEY_LOCAL_MACHINE\Software\Classes\
mimicfile\shell\open\
command
(Default) = notepad.exe %AppDataLocal%\Decrypt_ELENOR-corp_info.txt
HKEY_LOCAL_MACHINE\Software\Classes\
.ELENOR-corp-{Victim ID}
(Default) = mimicfile
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Run
systemsg.exe = notepad.exe %AppDataLocal%\Decrypt_ELENOR-corp_info.txt
该程序会修改以下注册表项:
HKEY_LOCAL_MACHINE\SOFTWARE\Policies\
Microsoft\Windows Defender
DisableAntiSpyware = 1
注:该注册表项的默认值为 0.)
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows Defender
DisableAntiSpyware = 1
注:该注册表项的默认值为 0.)
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\
services\WinDefend
Start = 3
注:该注册表项的默认值为 2.)
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\
Services\{Service with "sql","backup", or "database" in its Name}
Start = 4
HKEY_LOCAL_MACHINE\Software\Microsoft\
Windows\CurrentVersion\Policies\
Explorer
shutdownwithoutlogon = 0
注:该注册表项的默认值为 1.)
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Policies\
System
ConsentPromptBehaviorAdmin = 5
注:该注册表项的默认值为 5.)
HKEY_LOCAL_MACHINE\SOFTWARE\MICROSOFT\
Windows\CurrentVersion\Policies\
System
legalnoticetext = {Contents of Ransom Note}
注:该注册表项的默认值为 {Empty}.)
HKEY_LOCAL_MACHINE\SOFTWARE\MICROSOFT\
Windows\CurrentVersion\Policies\
System
legalnoticecaption = {Space}
注:该注册表项的默认值为 {Empty}.)
它会删除以下注册表项:
HKEY_LOCAL_MACHINE\Software\Policies\
Microsoft\Windows\System
DisableCmd =
HKEY_CURRENT_USER\Software\Policies\
Microsoft\Windows\System
DisableCmd =
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Run
systemsg.exe =
HKEY_CURRENT_USER\SOFTWARE\Microsoft\
Windows\CurrentVersion\Run
systemsg.exe =
Propagation
该勒索软件不具备任何传播功能。
Backdoor Routine
该勒索软件不具备任何后门功能。
Rootkit Capabilities
该勒索软件不具备Rootkit功能。
进程终止
若在受感染系统上发现以下服务,该勒索软件会将其终止:
- WSearch
- pla
- DusmSvc
- defragsvc
- DoSvc
- wercplsupport
- SDRSVC
- TroubleshootingSvc
- Wecsvc
- fhsvc
- wbengine
- PcaSvc
- WerSvc
- SENS
- AppIDSvc
- BITS
- wuauserv
- SysMain
- DiagTrack
- diagnosticshub.standalonecollector.service
- dmwappushservice
- WMPNetworkSvc
若在受感染系统的内存中发现以下进程正在运行,该勒索软件会将其终止:
- taskmgr.exe
- tasklist.exe
- taskkill.exe
- perfmon.exe
- Everything.exe
It terminates processes or services that contain any of the following strings if found running in the affected system's memory:
- sql
- backup
- database
Information Theft
This Ransomware gathers the following information on the affected computer:
- Processor architecture
- Number of processors
- RAM information
- OS version
- Username
- Computer name
- If executed with elevated privileges or not
- User groups
- Affected machine IP address
- Network adapter name
- Network shares
- Network drives
- If the full version of .NET Framework 4 is installed on the affected system or not
其他信息
该勒索软件会对以下扩展名的文件进行加密:
- tib
- sql
- sqlite
- sqlite3
- sqlitedb
- mdf
- mdb
- adb
- db
- db3
- dbf
- dbs
- udb
- dbv
- dbx
- edb
- exb
- 1cd
- fdb
- idb
- mpd
- myd
- odb
- xls
- xlsx
- doc
- docx
- bac
- bak
- back
- zip
- rar
- dt
- 4dd
- 4dl
- abcddb
- abs
- abx
- accdb
- accdc
- accde
- accdr
- accdt
- accdw
- accft
- ade
- adf
- adn
- adp
- alf
- arc
- ask
- bacpac
- bdf
- btr
- cat
- cdb
- chck
- ckp
- cma
- cpd
- dacpac
- dad
- dadiagrams
- daschema
- db-shm
- db-wal
- db2
- dbc
- dbt
- dcb
- dct
- dcx
- ddl
- dlis
- dp1
- dqy
- dsk
- dsn
- dtsx
- dxl
- eco
- ecx
- epim
- fcd
- fic
- fm5
- fmp
- fmp12
- fmpsl
- fol
- fp3
- fp4
- fp5
- fp7
- fpt
- frm
- gdb
- grdb
- gwi
- hdb
- his
- hjt
- ib
- icg
- icr
- ihx
- itdb
- itw
- jet
- jtx
- kdb
- kexi
- kexic
- kexis
- lgc
- lut
- lwx
- maf
- maq
- mar
- mas
- mav
- maw
- mdn
- mdt
- mrg
- mud
- mwb
- ndf
- nnt
- nrmlib
- ns2
- ns3
- ns4
- nsf
- nv
- nv2
- nwdb
- nyf
- oqy
- ora
- orx
- owc
- p96
- p97
- pan
- pdb
- pdm
- pnz
- qry
- qvd
- rbf
- rctd
- rod
- rodx
- rpd
- rsd
- s2db
- sas7bdat
- sbf
- scx
- sdb
- sdc
- sdf
- sis
- sl3
- spq
- sqlite2
- te
- temx
- tmd
- tps
- trc
- trm
- udl
- usr
- v12
- vis
- vpd
- vvv
- wdb
- wmdb
- wrk
- xdb
- data
- xld
- xmlff
- 7z
它会执行以下操作:
- It does not proceed with its behavior when the affected system's operating system is Windows XP or older.
- It uses the following GUI to control the operation of the ransomware:
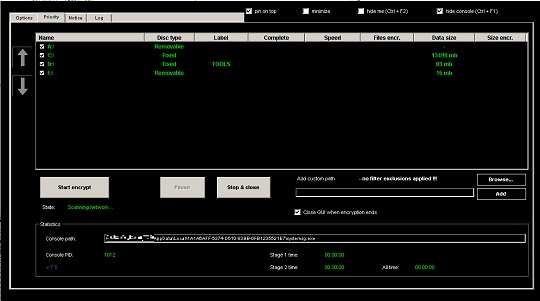
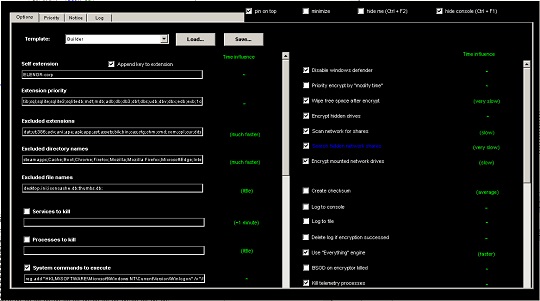
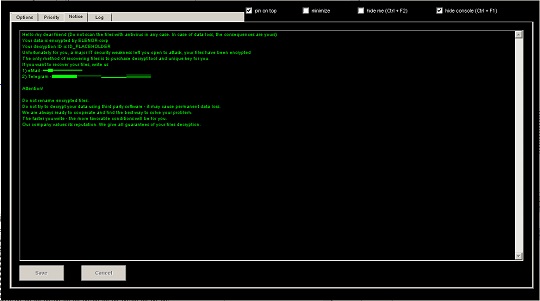
- It encrypts fixed and removable drives and network shares.
- It abuses Everything APIs to search for files to encrypt.
- It stores a session key in %AppDataLocal%\{Generated GUID}\session.tmp to resume encryption if the process is interrupted.
- It disables Windows Defender.
- It disables the affected system's ability to sleep, hibernate, or enter power-saving mode.
- It uses Powershell to stop all running VMs, identify VHDs associated with VMs and unmounts them.
- It empties the recycle bin.
- It uses WQL to delete volume shadow copies.
- It enables multiple remote desktop sessions to the affected system.
- It sets sethc.exe (Sticky Keys) to open cmd.exe.
- It clears security, system, and applicaiton event logs.
- It disables Windows telemetry.
- It sets itself to be one of the last processes terminated during system shutdown.
它接受以下参数:
- -dir → directory for encryption
- -e all → encrypt all (default)
- -e local → encrypt local files
- -e net → encrypt files on network drives
- -e watch
- -e share → encrypt files on network shares
- -e ul1 → unlock certain memory addresses from another process
- -e ul2 → unlock certain memory addresses from another process
- -prot → protects the ransomware from being killed
- -pid → process identifier (PID) of the previously-running ransomware
- -tail
它不会利用任何漏洞。
Ransomware Routine
此勒索软件会避免加密文件路径中包含以下字符串的文件:
- desktop.ini
- iconcache.db
- thumbs.db
- ntuser.ini
- boot.ini
- ntdetect.com
- ntldr
- NTUSER.DAT
- bootmgr
- BOOTNXT
- BOOTTGT
- session.tmp
- Decrypt_ELENOR-corp_info.txt
它会避免加密以下文件夹中的文件:
- steamapps
- Cache
- Boot
- Chrome
- Firefox
- Mozilla
- Mozilla Firefox
- MicrosoftEdge
- Internet Explorer
- TorBrowser
- Opera
- Opera Software
- Common Files
- Config.Msi
- Intel
- Microsoft
- Microsoft Shared
- Microsoft.NET
- MSBuild
- MSOCache
- Packages
- PerfLogs
- Program Files
- Program Files (x86)
- ProgramData
- System Volume Information
- tmp
- Temp
- USOShared
- Windows
- Windows Defender
- Windows Journal
- Windows NT
- Windows Photo Viewer
- Windows Security
- Windows.old
- WindowsApps
- WindowsPowerShell
- WINNT
- $RECYCLE.BIN
- $WINDOWS.~BT
- $Windows.~WS
- :\Users\Public\
- :\Users\Default\
- %AppDataLocal%\{Generated GUID}
(Note: %AppDataLocal% 是本地应用程序数据文件夹, 通常位于此路径 C:\Documents and Settings\{user name}\Local Settings\Application Data 在Windows 2000(32位)、XP及Server 2003(32位)系统上,或 C:\Users\{user name}\AppData\Local 在Windows Vista、7、8、8.1、2008(64位)、2012(64位)及10(64位)系统上。)
它会为加密文件的文件名添加以下扩展名:
- .ELENOR-corp-{Victim ID}
它会释放以下文件作为勒索信:
- {Root of Encrypted Path}\Decrypt_ELENOR-corp_info.txt
- %Desktop%\Decrypt_ELENOR-corp_info.txt
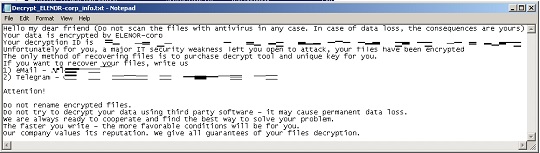
它会避免加密具有以下文件扩展名的文件:
- ELENOR-corp-{Victim ID}
- dat
- ut
- 386
- adv
- ani
- ape
- apk
- app
- asf
- assets
- bik
- bin
- cas
- cfg
- chm
- cmd
- com
- cpl
- cur
- dds
- deskthemepack
- diagcab
- diagcfg
- diagpkg
- dll
- dmp
- drv
- dsf
- epub
- exe
- fnt
- fon
- gif
- hlp
- hta
- htm
- html
- ico
- ics
- idx
- inf
- info
- ini
- ipch
- lib
- log
- manifest
- mid
- mod
- msc
- msi
- msp
- msstyles
- msu
- mui
- mxf
- nls
- nomedia
- ocx
- otf
- pak
- pif
- ps1
- py
- rc
- reg
- resource
- ress
- rgss3a
- rm
- rmvb
- rom
- rpa
- rpgmvo
- rpgmvp
- rpy
- rpyc
- rtf
- rtp
- rvdata2
- sfcache
- shs
- snd
- so
- swf
- sys
- tak
- theme
- themepack
- tiger
- tmp
- torrent
- ts
- ttc
- ttf
- h
- cpp
- unity3d
- usm
- vbs
- vob
- vsix
- wav
- winmd
- woff
- wpx
- wv
- xex
- xml
解决方案
Step 1
亚信安全测性机器学习可在恶意软件初现时、尚未在系统执行前便及时检测并拦截。启用此功能后,您的亚信安全产品会使用以下机器学习命名标识检测该恶意软件:
Step 2
在进行任何扫描之前,Windows 7、Windows 8、Windows 8.1 和 Windows 10 用户必须先执行以下操作: 禁用 系统还原 以便对电脑进行全面扫描。
Step 3
注意:在此恶意软件/间谍软件/灰色软件执行期间,并非所有文件、文件夹和注册表键值和项都会安装到您的计算机上。这可能是由于不完整的安装或其他操作系统条件所致。如果您没有找到相同的文件/文件夹/注册表信息,请继续进行下一步操作。
Step 4
以安全模式重启
要进入安全模式重启:
• For Windows 7 and Windows Server 2008 (R2) users
- 重启你的电脑。
- 按下F8 在开机自检(POST)程序完成后。如果 高级启动选项 若未出现菜单,请尝试重启计算机,并在POST界面显示后多次按F8键。
- 在高级启动选项菜单中,使用方向键选择Safe Mode 选项,然后按 Enter.
• For Windows 8, Windows 8.1, and Windows Server 2012 users
- 访问Charms bar 将鼠标指针移至屏幕右上角即可。
- 将鼠标指针向下移动并点击 Settings>更改您的电脑设置.
- 在左侧面板中,点击“通用”。
- 在右侧面板中,向下滚动至底部找到 Advanced startup 部分,然后点击 Restart now 按钮并等待系统重启。
- 在Advanced Startup 菜单中,点击 Troubleshoot>Advanced Options>Startup Settings>Restart 并等待系统重启。
- 在Startup Settings 菜单中,按下 4 以启用安全模式。
• 对于 Windows 10 用户:
- 按下Windows logo key + I 键打开“设置”。若无效,请选择 Start按钮,然后选择Settings.
- 选择Update & Security > Recovery.
- 在Advanced startup, select Restart now.
- 当您的电脑重启进入 请选择一个选项 屏幕上,选择Troubleshoot > Advcanced options > 启动设置 > Restart.
- 电脑重启后,您将看到一系列选项。请选择4 或按 F4 以安全模式启动您的电脑。
Step 5
删除此注册表值
Important: 编辑 Windows Registry 操作不当可能导致系统出现无法恢复的故障。请务必仅在您熟悉相关步骤的情况下执行;如有疑问,可寻求系统管理员的协助。否则,请查看下方链接。 Microsoft article 修改计算机注册表前请务必先进行此操作.
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
- systemsg = %AppDataLocal%\{Generated GUID}\systemsg.exe
- systemsg = %AppDataLocal%\{Generated GUID}\systemsg.exe
- In HKEY_LOCAL_MACHINE\SOFTWARE\Classes\exefile\shell\open\command
- (Default) = %1 %*
- (Default) = %1 %*
- In HKEY_USER\S-1-5-21-2019512041-4230814187-3178073052-1000_CLASSES\exefile\shell\open\command
- (Default) = %1 %*
- (Default) = %1 %*
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Defender\Real-Time Protection
- DisableRealtimeMonitoring = 1
- DisableRealtimeMonitoring = 1
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\SearchIndexer.exe
- Debugger = %System%\Systray.exe
- Debugger = %System%\Systray.exe
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\SearchProtocolHost.exe
- Debugger = %System%\Systray.exe
- Debugger = %System%\Systray.exe
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\SearchApp.exe
- Debugger = %System%\Systray.exe
- Debugger = %System%\Systray.exe
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\CompatTelRunner.exe
- Debugger = %System%\Systray.exe
- Debugger = %System%\Systray.exe
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\wsqmcons.exe
- Debugger = %System%\Systray.exe
- Debugger = %System%\Systray.exe
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\taskmgr.exe
- Debugger = %System%\Systray.exe
- Debugger = %System%\Systray.exe
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\tasklist.exe
- Debugger = %System%\Systray.exe
- Debugger = %System%\Systray.exe
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\taskkil.exe
- Debugger = %System%\Systray.exe
- Debugger = %System%\Systray.exe
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\perfmon.exe
- Debugger = %System%\Systray.exe
- Debugger = %System%\Systray.exe
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\shutdown.exe
- Debugger = %System%\Systray.exe
- Debugger = %System%\Systray.exe
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\logoff.exe
- Debugger = %System%\Systray.exe
- Debugger = %System%\Systray.exe
- In HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer
- HidePowerOptions = 1
- HidePowerOptions = 1
- In HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer
- HidePowerOptions = 1
- HidePowerOptions = 1
- In HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer
- NoClose = 1
- NoClose = 1
- In HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer
- StartMenuLogOff = 1
- StartMenuLogOff = 1
- In HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Control\FileSystem
- LongPathsEnabled = 1
- LongPathsEnabled = 1
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\DataCollection
- AllowTelemetry = 0
- AllowTelemetry = 0
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon
- AllowMultipleTSSessions = 1
- AllowMultipleTSSessions = 1
- In HKEY_LOCAL_MACHINE\system\CurrentControlSet\Control\Terminal Server
- fSingleSessionPerUser = 0
- fSingleSessionPerUser = 0
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\sethc.exe
- Debugger = c:\windows\system32\cmd.exe
- Debugger = c:\windows\system32\cmd.exe
- In HKEY_LOCAL_MACHINE\Software\Classes\mimicfile\shell\open\command
- (Default) = notepad.exe %AppDataLocal%\Decrypt_ELENOR-corp_info.txt
- (Default) = notepad.exe %AppDataLocal%\Decrypt_ELENOR-corp_info.txt
- In HKEY_LOCAL_MACHINE\Software\Classes\.ELENOR-corp-{Victim ID}
- (Dafault) = mimicfile
- (Dafault) = mimicfile
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
- systemsg.exe = notepad.exe %AppDataLocal%\Decrypt_ELENOR-corp_info.txt
- systemsg.exe = notepad.exe %AppDataLocal%\Decrypt_ELENOR-corp_info.txt
要删除此恶意软件创建的注册表值:
- 打开注册表编辑器。 为此,请执行以下操作:
» 对于 Windows 7 和 Windows Server 2008 (R2) 用户,请点击 Start button, type regedit in the Search输入字段,然后按下Enter.
» 对于 Windows 8、Windows 8.1、10 及 Windows Server 2012 (R2) 用户,请右键单击屏幕左下角,点击 Run, type regedit 在提供的文本框中,然后点击 Enter. - 在注册表编辑器窗口的左侧面板中,双击以下项目:
HKEY_LOCAL_MACHINE>SOFTWARE>Microsoft>Windows>CurrentVersion>Run - 在右侧面板中,找到并删除以下条目:
systemsg = %AppDataLocal%\{Generated GUID}\systemsg.exe - 在注册表编辑器窗口的左侧面板中,双击以下项目:
HKEY_LOCAL_MACHINE>SOFTWARE>Classes>exefile>shell>open>command - 在右侧面板中,找到并删除以下条目:
(Default) = %1 %* - 在注册表编辑器窗口的左侧面板中,双击以下项目:
HKEY_USER>S-1-5-21-2019512041-4230814187-3178073052-1000_CLASSES>exefile>shell>open>command - 在右侧面板中,找到并删除以下条目:
(Default) = %1 %* - 在注册表编辑器窗口的左侧面板中,双击以下项目:
HKEY_LOCAL_MACHINE>SOFTWARE>Microsoft>Windows Defender>Real-Time Protection - 在右侧面板中,找到并删除以下条目:
DisableRealtimeMonitoring = 1 - 在注册表编辑器窗口的左侧面板中,双击以下项目:
HKEY_LOCAL_MACHINE>SOFTWARE>Microsoft>Windows NT>CurrentVersion>Image File Execution Options>SearchIndexer.exe - 在右侧面板中,找到并删除以下条目:
Debugger = %System%\Systray.exe - 在注册表编辑器窗口的左侧面板中,双击以下项目:
HKEY_LOCAL_MACHINE>SOFTWARE>Microsoft>Windows NT>CurrentVersion>Image File Execution Options>SearchProtocolHost.exe - 在右侧面板中,找到并删除以下条目:
Debugger = %System%\Systray.exe - 在注册表编辑器窗口的左侧面板中,双击以下项目:
HKEY_LOCAL_MACHINE>SOFTWARE>Microsoft>Windows NT>CurrentVersion>Image File Execution Options>SearchApp.exe - 在右侧面板中,找到并删除以下条目:
Debugger = %System%\Systray.exe - 在注册表编辑器窗口的左侧面板中,双击以下项目:
HKEY_LOCAL_MACHINE>SOFTWARE>Microsoft>Windows NT>CurrentVersion>Image File Execution Options>CompatTelRunner.exe - 在右侧面板中,找到并删除以下条目:
Debugger = %System%\Systray.exe - 在注册表编辑器窗口的左侧面板中,双击以下项目:
HKEY_LOCAL_MACHINE>SOFTWARE>Microsoft>Windows NT>CurrentVersion>Image File Execution Options>wsqmcons.exe - 在右侧面板中,找到并删除以下条目:
Debugger = %System%\Systray.exe - 在注册表编辑器窗口的左侧面板中,双击以下项目:
HKEY_LOCAL_MACHINE>SOFTWARE>Microsoft>Windows NT>CurrentVersion>Image File Execution Options>taskmgr.exe - 在右侧面板中,找到并删除以下条目:
Debugger = %System%\Systray.exe - 在注册表编辑器窗口的左侧面板中,双击以下项目:
HKEY_LOCAL_MACHINE>SOFTWARE>Microsoft>Windows NT>CurrentVersion>Image File Execution Options>tasklist.exe - 在右侧面板中,找到并删除以下条目:
Debugger = %System%\Systray.exe - 在注册表编辑器窗口的左侧面板中,双击以下项目:
HKEY_LOCAL_MACHINE>SOFTWARE>Microsoft>Windows NT>CurrentVersion>Image File Execution Options>taskkil.exe - 在右侧面板中,找到并删除以下条目:
Debugger = %System%\Systray.exe - 在注册表编辑器窗口的左侧面板中,双击以下项目:
HKEY_LOCAL_MACHINE>SOFTWARE>Microsoft>Windows NT>CurrentVersion>Image File Execution Options>perfmon.exe - 在右侧面板中,找到并删除以下条目:
Debugger = %System%\Systray.exe - 在注册表编辑器窗口的左侧面板中,双击以下项目:
HKEY_LOCAL_MACHINE>SOFTWARE>Microsoft>Windows NT>CurrentVersion>Image File Execution Options>shutdown.exe - 在右侧面板中,找到并删除以下条目:
Debugger = %System%\Systray.exe - 在注册表编辑器窗口的左侧面板中,双击以下项目:
HKEY_LOCAL_MACHINE>SOFTWARE>Microsoft>Windows NT>CurrentVersion>Image File Execution Options>logoff.exe - 在右侧面板中,找到并删除以下条目:
Debugger = %System%\Systray.exe - 在注册表编辑器窗口的左侧面板中,双击以下项目:
HKEY_LOCAL_MACHINE>Software>Microsoft>Windows>CurrentVersion>Policies>Explorer - 在右侧面板中,找到并删除以下条目:
HidePowerOptions = 1 - 在注册表编辑器窗口的左侧面板中,双击以下项目:
HKEY_CURRENT_USER>Software>Microsoft>Windows>CurrentVersion>Policies>Explorer - 在右侧面板中,找到并删除以下条目:
HidePowerOptions = 1 - Again 在右侧面板中,找到并删除以下条目:
NoClose = 1 - Again 在右侧面板中,找到并删除以下条目:
StartMenuLogOff = 1 - 在注册表编辑器窗口的左侧面板中,双击以下项目:
HKEY_LOCAL_MACHINE>SYSTEM>ControlSet001>Control>FileSystem - 在右侧面板中,找到并删除以下条目:
LongPathsEnabled = 1 - 在注册表编辑器窗口的左侧面板中,双击以下项目:
HKEY_LOCAL_MACHINE>SOFTWARE>Microsoft>Windows>CurrentVersion>Policies>DataCollection - 在右侧面板中,找到并删除以下条目:
AllowTelemetry = 0 - 在注册表编辑器窗口的左侧面板中,双击以下项目:
HKEY_LOCAL_MACHINE>SOFTWARE>Microsoft>Windows NT>CurrentVersion>Winlogon - 在右侧面板中,找到并删除以下条目:
AllowMultipleTSSessions = 1 - 在注册表编辑器窗口的左侧面板中,双击以下项目:
HKEY_LOCAL_MACHINE>system>CurrentControlSet>Control>Terminal Server - 在右侧面板中,找到并删除以下条目:
fSingleSessionPerUser = 0 - 在注册表编辑器窗口的左侧面板中,双击以下项目:
HKEY_LOCAL_MACHINE>SOFTWARE>Microsoft>Windows NT>CurrentVersion>Image File Execution Options>sethc.exe - 在右侧面板中,找到并删除以下条目:
Debugger = c:\windows\system32\cmd.exe - 在注册表编辑器窗口的左侧面板中,双击以下项目:
HKEY_LOCAL_MACHINE>Software>Classes>mimicfile>shell>open>command - 在右侧面板中,找到并删除以下条目:
(Default) = notepad.exe %AppDataLocal%\Decrypt_ELENOR-corp_info.txt - 在注册表编辑器窗口的左侧面板中,双击以下项目:
HKEY_LOCAL_MACHINE>Software>Classes>.ELENOR-corp-{Victim ID} - 在右侧面板中,找到并删除以下条目:
(Dafault) = mimicfile - Again 在右侧面板中,找到并删除以下条目:
systemsg.exe = notepad.exe %AppDataLocal%\Decrypt_ELENOR-corp_info.txt - 关闭注册表编辑器。
Step 6
恢复这些被修改的注册表值
Important:Editing the Windows Registry 操作不当可能导致不可逆的系统故障。请仅在掌握操作技能时执行,或向系统管理员寻求帮助。's help. You may also check out this Microsoft article 修改计算机注册表前请务必先进行此操作.
- In HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows Defender
- From: DisableAntiSpyware = 1
To: DisableAntiSpyware = 0
- From: DisableAntiSpyware = 1
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Defender
- From: DisableAntiSpyware = 1
To: DisableAntiSpyware = 0
- From: DisableAntiSpyware = 1
- In HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\WinDefend
- From: Start = 3
To: Start = 2
- From: Start = 3
- In HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\{Service with sql,backup, or database in its Name}
- From: Start = 4
To: Start = {Default}
- From: Start = 4
- In HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer
- From: shutdownwithoutlogon = 0
To: shutdownwithoutlogon = 1
- From: shutdownwithoutlogon = 0
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System
- From: legalnoticetext = {Contents of Ransom Note}
To: legalnoticetext = {Empty}
- From: legalnoticetext = {Contents of Ransom Note}
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System
- From: legalnoticecaption = {Space}
To: legalnoticecaption = {Empty}
- From: legalnoticecaption = {Space}
To restore registry values this malware/grayware modified:
- Open Registry Editor. 为此,请执行以下操作:
- On Windows 7 and Server 2008 (R2):
点击Start button, type REGEDIT in the Search输入字段,然后按下Enter. - On Windows 8, 8.1, 10, and Server 2012 (R2):
右键点击屏幕左下角并单击 Run, type REGEDIT in the Run input field, and then press Enter.
- On Windows 7 and Server 2008 (R2):
- 在左侧面板中,双击以下项目:
HKEY_LOCAL_MACHINE>SOFTWARE>Policies>Microsoft>Windows Defender - 在右侧面板中,找到注册表值:
DisableAntiSpyware = 1 - Right-click on the value name 并选择“修改”。更改 value data of this entry to:
DisableAntiSpyware = 0 - 在左侧面板中,双击以下项目:
HKEY_LOCAL_MACHINE>SOFTWARE>Microsoft>Windows Defender - 在右侧面板中,找到注册表值:
DisableAntiSpyware = 1 - Right-click on the value name 并选择“修改”。更改 value data of this entry to:
DisableAntiSpyware = 0 - 在左侧面板中,双击以下项目:
HKEY_LOCAL_MACHINE>SYSTEM>ControlSet001>services>WinDefend - 在右侧面板中,找到注册表值:
Start = 3 - Right-click on the value name 并选择“修改”。更改 value data of this entry to:
Start = 2 - 在左侧面板中,双击以下项目:
HKEY_LOCAL_MACHINE>SYSTEM>CurrentControlSet>Services>{Service with sql,backup, or database in its Name} - 在右侧面板中,找到注册表值:
Start = 4 - Right-click on the value name 并选择“修改”。更改 value data of this entry to:
Start = {Default} - 在左侧面板中,双击以下项目:
HKEY_LOCAL_MACHINE>Software>Microsoft>Windows>CurrentVersion>Policies>Explorer - 在右侧面板中,找到注册表值:
shutdownwithoutlogon = 0 - Right-click on the value name 并选择“修改”。更改 value data of this entry to:
shutdownwithoutlogon = 1 - 在左侧面板中,双击以下项目:
HKEY_LOCAL_MACHINE>SOFTWARE>MICROSOFT>Windows>CurrentVersion>Policies>System - 在右侧面板中,找到注册表值:
legalnoticetext = {Contents of Ransom Note} - Right-click on the value name 并选择“修改”。更改 value data of this entry to:
legalnoticetext = {Empty} - Again 在右侧面板中,找到注册表值:
legalnoticecaption = {Space} - Right-click on the value name 并选择“修改”。更改 value data of this entry to:
legalnoticecaption = {Empty} - 关闭注册表编辑器。
Step 7
请从备份中恢复这些已删除的注册表项/值
*Note: 仅会恢复与微软相关的注册表项/值。如果恶意软件/灰色软件还删除了非微软程序的注册表项/值,请重新安装这些程序。
- In HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\System
- DisableCmd
- DisableCmd
- In HKEY_CURRENT_USER\Software\Policies\Microsoft\Windows\System
- DisableCmd
- DisableCmd
Step 8
搜索并删除这些文件
- %User Temp%\7ZipSfx.000\7za.exe
- %User Temp%\7ZipSfx.000\DC.exe
- %User Temp%\7ZipSfx.000\ENC_default_default_2024-09-01_14-25-56=ELENOR-corp.exe
- %User Temp%\7ZipSfx.000\Everything.exe
- %User Temp%\7ZipSfx.000\Everything.ini
- %User Temp%\7ZipSfx.000\Everything2.ini
- %User Temp%\7ZipSfx.000\Everything32.dll
- %User Temp%\7ZipSfx.000\Everything64.dll
- %User Temp%\7ZipSfx.000\gui35.exe
- %User Temp%\7ZipSfx.000\gui40.exe
- %User Temp%\7ZipSfx.000\xdel.exe
- %User Temp%\7ZSfx000.cmd
- %AppDataLocal%\{Generated GUID}\7za.exe
- %AppDataLocal%\{Generated GUID}\DC.exe
- %AppDataLocal%\{Generated GUID}\Everything.exe
- %AppDataLocal%\{Generated GUID}\Everything.ini
- %AppDataLocal%\{Generated GUID}\Everything2.ini
- %AppDataLocal%\{Generated GUID}\Everything32.dll
- %AppDataLocal%\{Generated GUID}\Everything64.dll
- %AppDataLocal%\{Generated GUID}\gui35.exe
- %AppDataLocal%\{Generated GUID}\gui40.exe
- %AppDataLocal%\{Generated GUID}\systemsg.exe
- %AppDataLocal%\{Generated GUID}\xdel.exe
- %AppDataLocal%\{Generated GUID}\session.tmp
- %AppDataLocal%\{Generated GUID}\global_options.ini
- %System%\GroupPolicy\Machine\Registry.pol
- %System%\GroupPolicy\gpt.ininerated GUID}
- %System Root%\temp\session.tmp
要删除恶意软件/灰色软件文件:
适用于 Windows 7、Server 2008 (R2)、8、8.1、10 及 Server 2012 (R2) 系统:
- 打开 Windows 资源管理器窗口。
- 对于 Windows 7 和 Server 2008 (R2) 用户:点击Start>Computer.
- 对于Windows 8、8.1、10及Server 2012用户, 右键单击屏幕左下角,然后点击 File Explorer.
- 在搜索计算机/此电脑输入框中,键入:
- %User Temp%\7ZipSfx.000\7za.exe
- %User Temp%\7ZipSfx.000\DC.exe
- %User Temp%\7ZipSfx.000\ENC_default_default_2024-09-01_14-25-56=ELENOR-corp.exe
- %User Temp%\7ZipSfx.000\Everything.exe
- %User Temp%\7ZipSfx.000\Everything.ini
- %User Temp%\7ZipSfx.000\Everything2.ini
- %User Temp%\7ZipSfx.000\Everything32.dll
- %User Temp%\7ZipSfx.000\Everything64.dll
- %User Temp%\7ZipSfx.000\gui35.exe
- %User Temp%\7ZipSfx.000\gui40.exe
- %User Temp%\7ZipSfx.000\xdel.exe
- %User Temp%\7ZSfx000.cmd
- %AppDataLocal%\{Generated GUID}\7za.exe
- %AppDataLocal%\{Generated GUID}\DC.exe
- %AppDataLocal%\{Generated GUID}\Everything.exe
- %AppDataLocal%\{Generated GUID}\Everything.ini
- %AppDataLocal%\{Generated GUID}\Everything2.ini
- %AppDataLocal%\{Generated GUID}\Everything32.dll
- %AppDataLocal%\{Generated GUID}\Everything64.dll
- %AppDataLocal%\{Generated GUID}\gui35.exe
- %AppDataLocal%\{Generated GUID}\gui40.exe
- %AppDataLocal%\{Generated GUID}\systemsg.exe
- %AppDataLocal%\{Generated GUID}\xdel.exe
- %AppDataLocal%\{Generated GUID}\session.tmp
- %AppDataLocal%\{Generated GUID}\global_options.ini
- %System%\GroupPolicy\Machine\Registry.pol
- %System%\GroupPolicy\gpt.ininerated GUID}
- %System Root%\temp\session.tmp
- 定位到该文件后,选中并按 SHIFT+DELETE 将其删除。
- 对所有列出的文件重复上述步骤。
*Note:阅读以下微软官方页面 若上述步骤在 Windows 7 和 Server 2008 (R2) 系统上无效:
Step 9
请搜索并删除以下文件夹:
- %User Temp%\7ZipSfx.000
- %AppDataLocal%\{Generated GUID}
- %System Root%\temp
要删除恶意软件/灰色软件/间谍软件文件夹:
适用于 Windows 7、Windows Server 2008 (R2)、Windows 8、Windows 8.1、Windows 10 及 Windows Server 2012 (R2):
- 打开 Windows 资源管理器窗口。
- 对于 Windows 7 和 Server 2008 (R2) 用户:点击Start>Computer.
- 对于 Windows 8、8.1、10 及 Server 2012 (R2) 用户: 右键单击 屏幕左下角,然后点击File Explorer.
- 在搜索计算机/此电脑输入框中,键入:
- %User Temp%\7ZipSfx.000
- %AppDataLocal%\{Generated GUID}
- %System Root%\temp
- 定位到该文件后,选中并按 SHIFT+DELETE 以永久删除该文件夹。
- 对剩余文件夹重复步骤2-3:
- %User Temp%\7ZipSfx.000
- %AppDataLocal%\{Generated GUID}
- %System Root%\temp
Step 10
以正常模式重启计算机,并使用亚信安全产品扫描检测病毒Ransom.Win32.MIMIC.D. 如果检测到的文件已被亚信安全产品清理、删除或隔离,则无需执行其他操作。您可以选择直接删除隔离文件。请勾选此项知识库页面 了解更多信息。
Step 11
从备份中还原加密文件。


