Ransom.Win32.NOKO.THDABBC
Ransom:Win32/Nokonoko.PB!MTB (MICROSOFT); Win32:Nokoyawa-A [Trj] (AVAST)
Windows


恶意软件类型:
Ransomware
有破坏性?:
没有
加密?:
没有
In the Wild:
是的
概要
它以文件的形式出现在系统中,可能是其他恶意软件投放的,或者是用户在访问恶意网站时无意中下载的。
技术详细信息
新病毒详细信息
它以文件的形式出现在系统中,可能是其他恶意软件投放的,或者是用户在访问恶意网站时无意中下载的。
安装
它添加下列进程:
- if --safe-mode commandline parameter is used:
- "%System%\bcdedit.exe" /set {default} safeboot network
- "%System%\shutdown.exe" -r
(注意: %System% 是 Windows 的 system 文件夹,通常位于 C:\Windows\System (Windows 98 和 ME)、C:\WINNT\System32 (Windows NT 和 2000) 和 C:\WINDOWS\system32 (Windows 2000(32-bit)、XP、Server 2003(32-bit)、Vista、7、8、8.1、2008(64-bit),2012(64bit) 和 10(64-bit))。)
自启动技术
它通过添加下列注册表项,注册为系统服务,确保在每次系统启动时自动执行:
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\
Control\SafeBoot\Network\
nokonoko → if --safe-mode commandline parameter is used.
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\
Services\nokonoko → if --safe-mode commandline parameter is used.
其他系统修改
它修改下列注册表项:
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\
Control\SafeBoot\Network\
nokonoko → if --safe-mode commandline parameter is used.
(Default) = Service
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\
Control → if --safe-mode commandline parameter is used.
ServicesPipeTimeout = 86400000
其他详细信息
该程序执行以下操作:
- It encrypts files found in the following drives:
- Fixed Drives
- Removable Drives
- Remote (Network) Drives
- The following can be changed in the runtime configuration:
- Directories to avoid
- File extensions to avoid
- Ransom note content
- Ransom note filename
- Appended extension of encrypted files
- Encryption of network shares
- Delete shadow copies
- Loading of hidden drives
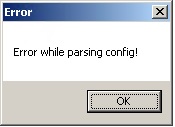
- It shows the following message box when the --config argument is improperly encoded:
- It adds the following service if --safe-mode commandline parameter is used:
- Service Name: nokonoko
Display Name: shmokoshmoko
Path to exectuable: {Malware File Path}\{Malware File Name}.exe --config {Base64 encoded config}
Start Type: Auto start
解决方案
Step 2
对于Windows ME和XP用户,在扫描前,请确认已禁用系统还原功能,才可全面扫描计算机。
Step 3
注意:在此恶意软件/间谍软件/灰色软件执行期间,并非所有文件、文件夹和注册表键值和项都会安装到您的计算机上。这可能是由于不完整的安装或其他操作系统条件所致。如果您没有找到相同的文件/文件夹/注册表信息,请继续进行下一步操作。
Step 4
重启进入安全模式
Step 5
恢复该修改的注册表值
注意事项:错误编辑Windows注册表会导致不可挽回的系统故障。只有在您掌握后或在系统管理员的帮助下才能完成这步。或者,请先阅读Microsoft文章,然后再修改计算机注册表。
- In HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Control\SafeBoot\Network\nokonoko
- (Default) = Service
- (Default) = Service
- In HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Control
- ServicesPipeTimeout = 86400000
- ServicesPipeTimeout = 86400000
Step 6
删除该注册表键值
注意事项:错误编辑Windows注册表会导致不可挽回的系统故障。只有在您掌握后或在系统管理员的帮助下才能完成这步。或者,请先阅读Microsoft文章,然后再修改计算机注册表。
- In HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Control\SafeBoot\Network\nokonoko
- In HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\nokonoko
Step 7
搜索和删除这些文件
- {Encrypted Directory}\NOKONOKO-readme.txt
- {Encrypted Directory}\NOKONOKO-readme.txt
Step 8
重启进入正常模式,使用亚信安全产品扫描计算机,检测Ransom.Win32.NOKO.THDABBC文件 如果检测到的文件已被亚信安全产品清除、删除或隔离,则无需采取进一步措施。可以选择直接删除隔离的文件。请参阅知识库页面了解详细信息。
Step 9
从备份中恢复加密文件。


