Ransom.Win32.RTMCOMMAND.THKBFBD
Ransom:Win32/RTMLocker.AA!MTB
Windows


恶意软件类型:
Ransomware
有破坏性?:
没有
加密?:

In the Wild:
是的
概要
它以文件的形式出现在系统中,可能是其他恶意软件投放的,或者是用户在访问恶意网站时无意中下载的。
技术详细信息
???????
It arrives on a system as a file dropped by other malware or as a file downloaded unknowingly by users when visiting malicious sites.
??
???????:
- %User Temp%\img{3 Random Characters}.tmp
(??: %User Temp% ?????? Temp ???????? C:\Documents and Settings\{user name}\Local Settings\Temp (Windows 2000(32-bit)?XP ? Server 2003(32-bit))?C:\Users\{user name}\AppData\Local\Temp (Windows Vista?7?8?8.1?2008(64-bit)?2012(64-bit) ? 10(64-bit)?)
???????:
- %System%\cmd.exe" /c PING -n 5 127.0.0.1 > NUL && del "{Malware Full Path}" ? deletes itself
(??: %System% ? Windows ? system ???,???? C:\Windows\System (Windows 98 ? ME)?C:\WINNT\System32 (Windows NT ? 2000) ? C:\WINDOWS\system32 (Windows 2000(32-bit)?XP?Server 2003(32-bit)?Vista?7?8?8.1?2008(64-bit),2012(64bit) ? 10(64-bit))?)
??????
???????????,??????:
HKEY_CURRENT_USER\Control Panel\Desktop
Wallpaper = %User Temp%\img{3 Random Characters}.tmp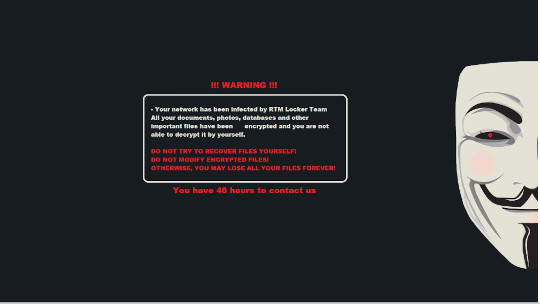
????
??????????????????:
- vss
- sql
- svc$
- memtas
- mepocs
- sophos
- veeam
- backup
- GxVss
- GxBlr
- GxFWD
- GxCVD
- GxCIMgr
- DefWatch
- ccEvtMgr
- ccSetMgr
- SavRoam
- RTVscan
- QBFCService
- QBIDPService
- Intuit
- QuickBooks
- FCS
- QBCFMonitorService
- YooBackup
- YooIT
- zhudongfangyu
- stc_raw_agent
- VSNAPVSS
- VeeamTransportSvc
- VeeamDeploymentService
- VeeamNFSSvc
- PDVFSService
- BackupExecVSSProvider
- BackupExecAgentAccelerator
- BackupExecAgentBrowser
- BackupExecDiveciMediaService
- BackupExecJobEngine
- BackupExecManagementService
- BackupExecRPCService
- AcrSch2Svc
- AcronisAgent
- CASAD2DWebSvc
- CAARCUpdateSvc
????????????????????:
- sql.exe
- oracle.exe
- ocssd.exe.
- dbsnmp.exe
- synctime.exe
- agntsvc.exe
- isqlplussvc.exe
- xfssvccon.exe
- mydesktopservice.exe
- ocautoupds.exe
- encsvc.exe
- firefox.exe
- tbirdconfig.exe
- mydesktopqos.exe
- ocomm.exe
- dbeng50.exe
- sqbcoreservice.exe
- excel.exe
- infopath.exe
- msaccess.exe
- mspub.exe
- onenote.exe
- outlook.exe
- powerpnt.exe
- steam.exe
- thebat.exe
- thunderbird.exe
- visio.exe
- winword.exe
- wordpad.exe
- notepad.exe
??????
?????????:
- It encrypts all available drives except CDROM
- It does not encrypt files with filesize below 512 Bytes
- It can only encrypt up to 8000 bytes of content only
- Empties Recycle Bin
- If not executed with admins rights, it will relaunch itself as admin using this command:
- %System%\cmd.exe /c ECHO “You must restart the program to resolve a critical error” && start”” ” %System Root%\{Malware Full path}.exe”
- Clear event logs for the following:
- System
- Application
- Security
(??: %System Root% ?????,???? C:\??????????????)
解决方案
Step 2
??Windows ME?XP??,????,????????????,??????????
Step 3
注意:在此恶意软件/间谍软件/灰色软件执行期间,并非所有文件、文件夹和注册表键值和项都会安装到您的计算机上。这可能是由于不完整的安装或其他操作系统条件所致。如果您没有找到相同的文件/文件夹/注册表信息,请继续进行下一步操作。
Step 4
????????
- %User Temp%\img{3 Random Characters.tmp}
- {Encrypted directory}\How To Restore Your Files.txt
Step 5
??????
Step 6
从备份中恢复加密文件。
Step 7
????????,?????????????,??Ransom.Win32.RTMCOMMAND.THKBFBD?? ????????????????????????,????????????????????????????????????????


