WikiLeaks Twitter Spam
After the WikiLeaks publication of a confidential document that has created a global stir, spammers are now taking advantage of the event. As with most social engineering attacks, cybercriminals are not too far behind every time something hot comes up.
As proof of this, TrendLabs recently received several types of spammed messages related to the WikiLeaks issue.
Wikileak Malware Spam
The spammed messages appear like they came come from WikiLeak, as indicated in the From field. It bears “IRAN Nuclear BOMB!” as its subject and contains the URLhxxp://wikileaks1.{BLOCKED}a.com, which has been verified as malicious. The URL is related tohxxp://ugo.{BLOCKED}e.com/226.exe, which has been classified as a disease vector and downloads a file, which has been submitted to the FRS team for analysis.
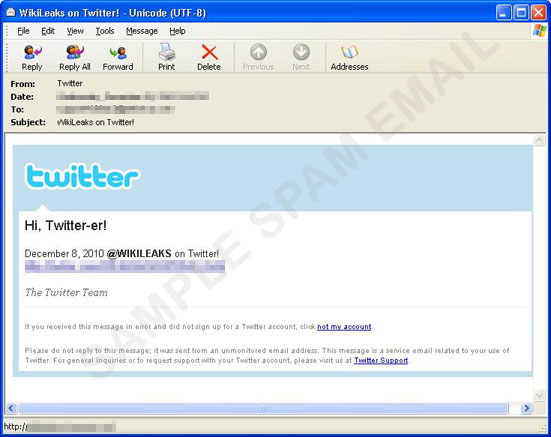
WikiLeaks on Twitter
Another slew of spammed messages appear to have come from Twitter. It features the subject, “WikiLeaks on Twitter!” and a link that seems direct to the WikiLeak Twitter pagehxxp://twitter.com/WIKILEAKS/4QHW-SRUS83. In reality, however, it connects tohttp://{BLOCKED}sbargainworld.net/, a site selling pharmaceutical product. The spammers behind the attack used an anchor tag to hide the real URL.
Spammed messages are already detected using the Full Pattern AS 7818 released on December 8, 2010 11:29PM (GMT 8)
- TMASE引擎(全局:6.5
- TMASE样式(全局):7818
