QAKBOT Attacks Continue to Spread Through Microsoft's OneNote App
2023年2月10日
Early in 2023, there started a rise of malware campaigns that used and abused Microsoft's Note-taking Application, OneNote. One of the malware families that took advantage of this time is QAKBOT, a banking trojan that is known for being a conduit for delivering other payload into a victim's device. The method of propagation this campaign has chosen is email, where malware is disguised as a OneNote email attachment that actually direct to a malicious OneNote Document. The threat actor group TA577 has been leveraging this technique so that if left unattended it will only be a matter of time before other threat actors start using this spam technique.

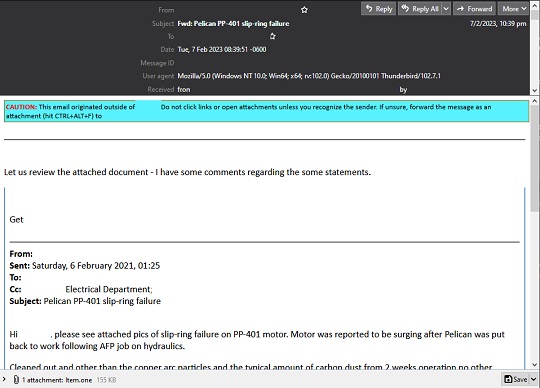
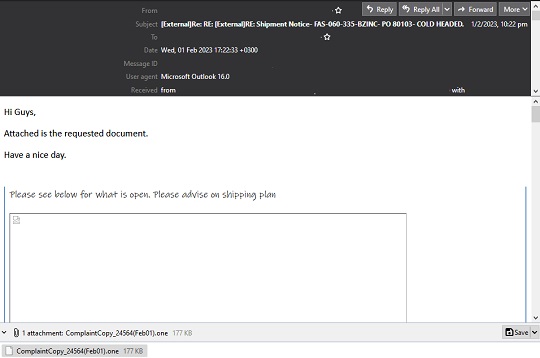
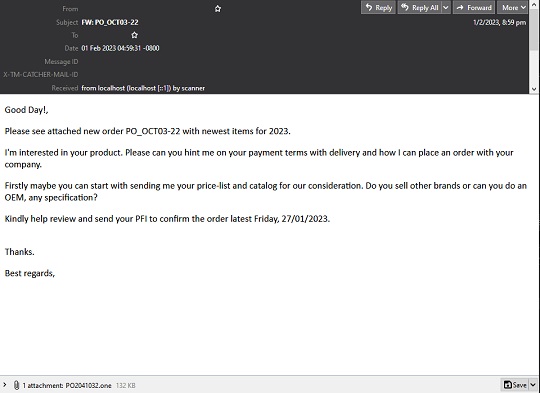
This spam campaign uses social engineering tactics wherein threat actors entice victims to check and click a malicious attachment. To make their campaign more believable, they have linked their emails to topics like remittances, shipping documents, and seasonal documents like HR Memos. The attack is well thought out and have been seen to target the manufacturing industry and educational institutions. Another technique that the threat actors use is email thread-hijacking to make it appear that their email is already part of an existing thread making their victim even more convinced into thinking that the malicious attachment is legitimate. Lastly, the threat actors opt to 'Reply All' in hijacked threads in order to spread copies of this malware to more potential victims and increase their reach exponentially.



The Badware OneNote attachment is detected as QAKBOT. This Malware is known to compromise a victim's machine and run a malicious script that downloads and runs a malicious file that then connects to different IP addresses and start to distribute payloads. The payload of this spam campaign include but are not limited to known malware families Redline, AsyncRAT, and Blackbasta which are designed to steal personal information from victims.
The infection chain goes as follows:
- An email with the malicious OneNote Doucment is received by the victim.
- The victim clicks or downloads the file attachment and allows the malicious script to run.
- The malware will download and run a DLL file which is disguised as an Image file.
- Victim's device is now compromised and malware will connect to different IP address to deliver more payload.
Here are some of the URLs the malware is known to
retrieve malicious DLL and other payloads from:
- hxxp://61[.]166[.]221[.]46:995/t5
- hxxp://197[.]94[.]67[.]207:443/t5
- hxxp://186[.]64[.]67[.]6:443/t5
- hxxp://finetuning-digital[.]com/wRuLe/01[.]gif
- hxxp://autovanin[.]com/YAGP/01[.]gif
- hxxp://tinintrep[.]ro/v4yx2g/01[.]gif
These Spam mails under this campaign are already detected by Trend Micro Email Security Solutions. Additionally, the Trojan is already detected by Trend Micro. We further recommend to never open suspicious files attached in emails and links.
垃圾邮件阻止日期/时间 : 2023年2月10日 22:37:00 GMT-8
TMASE
- TMASE引擎(全局:9.0.1004
- TMASE样式(全局):7440.000
